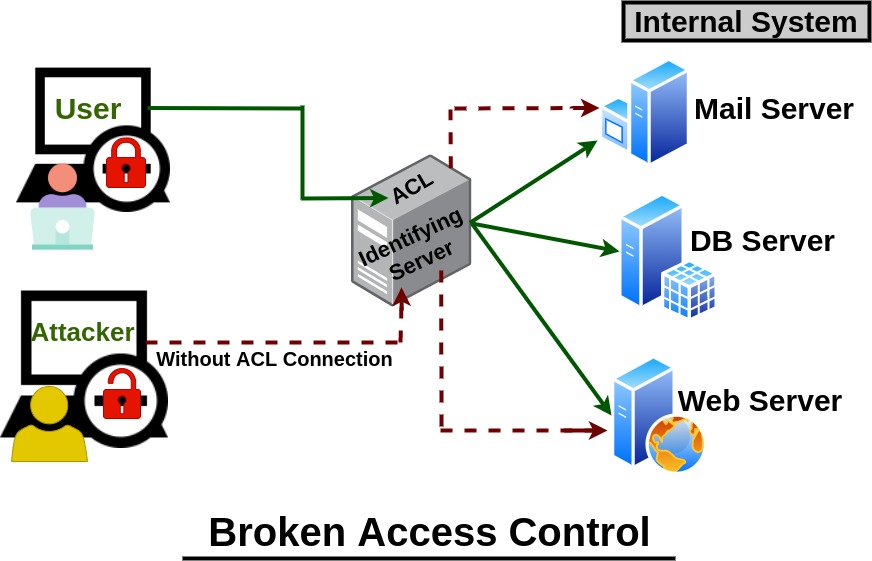
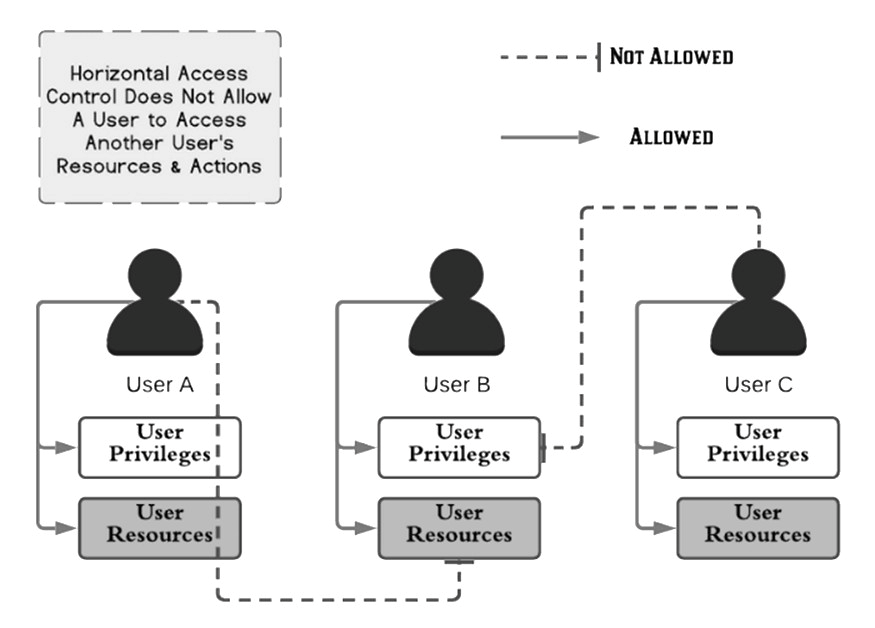
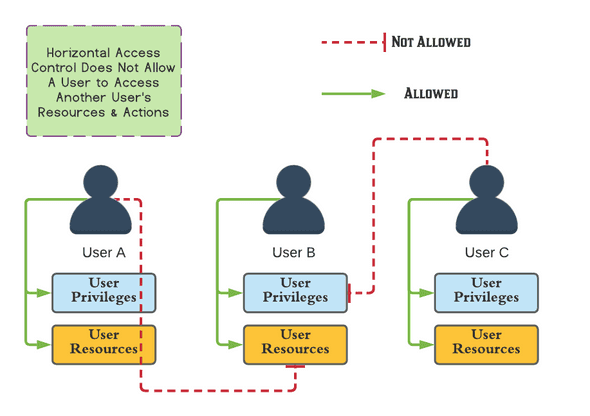
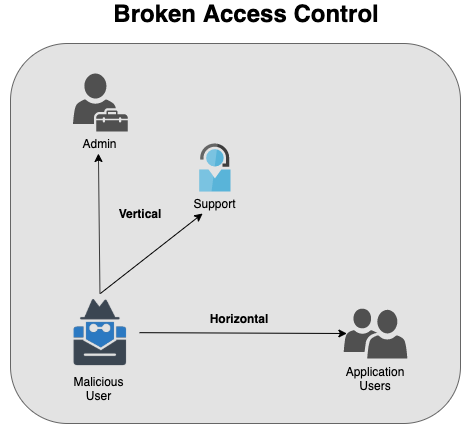
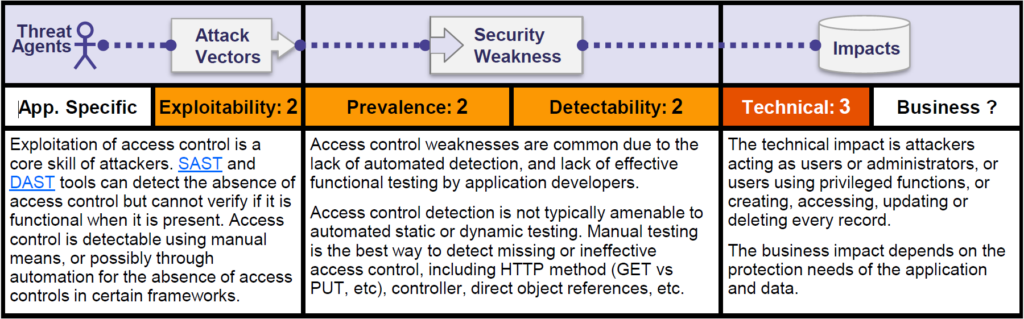
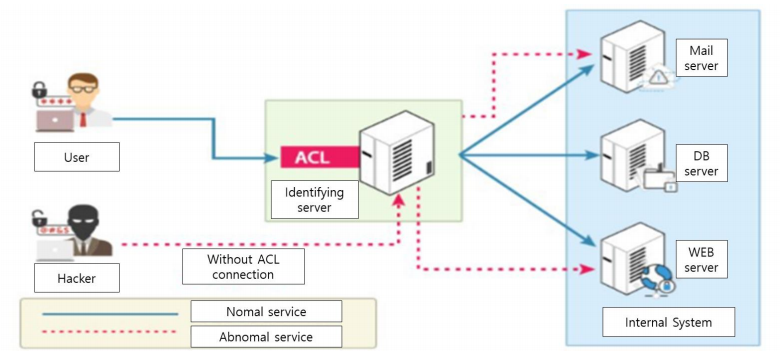
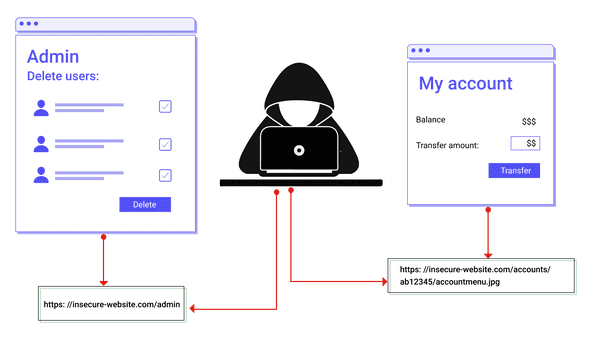
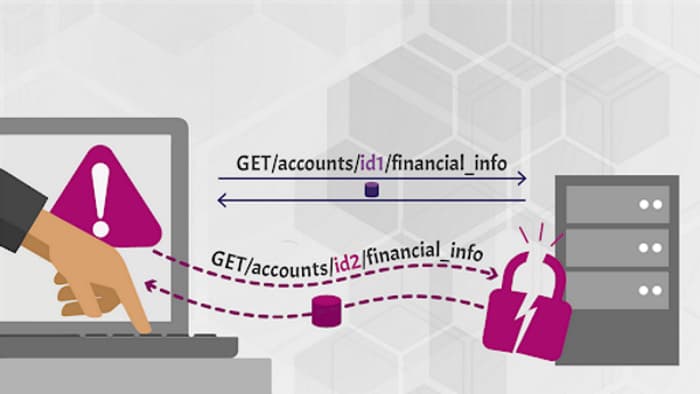
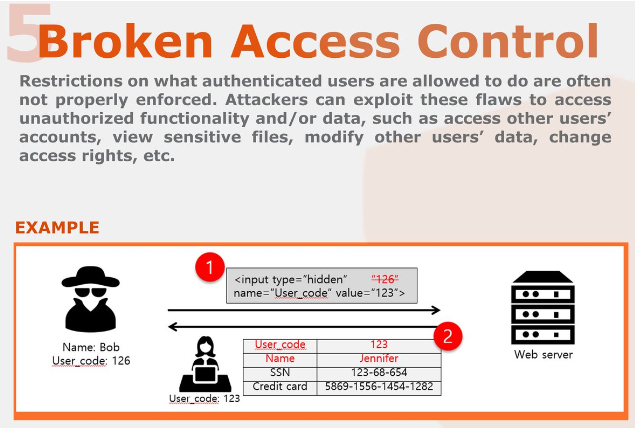
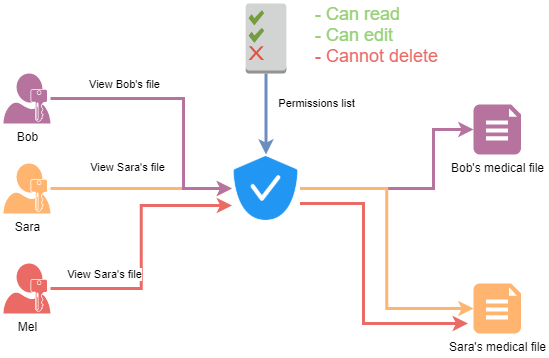
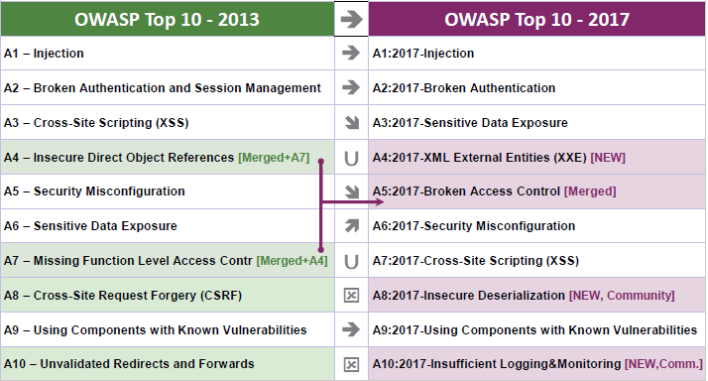
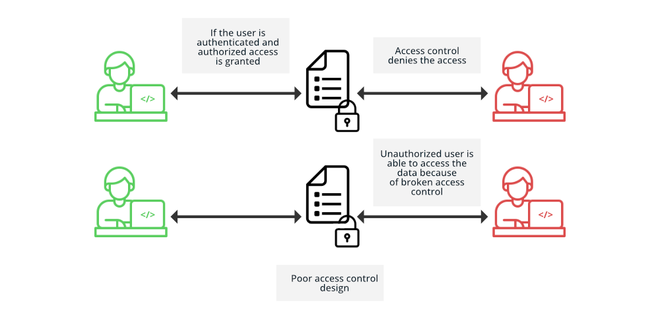
Safe Decision Co. on X: "#Web Application Security Risks. 5-Broken Access Control: #CyberSecurity https://t.co/cYHfvcrKCD" / X

Malaysia IT Professional Network - Broken Access Control is listed under OWASP Top 10, thus the need for web security is real. To gain more on the best practices to combat incoming